Updated – July 2024
In today’s digital landscape, securing sensitive data and ensuring only the right people have access to it is more critical than ever. This is where Azure Entra ID’s Privileged Identity Management (PIM) comes into play. Let’s break down what this service is, why you need it, and how it can help your organisation stay secure and compliant.
What is Privileged Identity Management (PIM)?
Privileged Identity Management (PIM) is a feature in Azure Entra ID (formerly known as Azure Active Directory) that helps you manage, control, and monitor access to important resources in your organisation. This includes access to Azure resources, Microsoft 365, and other SaaS applications integrated with Azure Entra ID.
Think of PIM as a security guard for your IT infrastructure, ensuring that only the right people have the keys to the castle – and only when they really need them.
Why is PIM Needed?
Imagine you have a large team of administrators who need access to critical systems, but only occasionally. If they always have elevated permissions, this poses a significant security risk. Accidental deletions, malicious attacks, or compliance breaches become more likely.
PIM addresses this by providing just-in-time (JIT) access to administrators. This means users get the access they need only when they need it and for a limited time. Here’s why this is important:
- Reduced Risk: Minimising the duration of elevated access reduces the window of opportunity for potential attacks.
- Compliance: PIM helps you meet compliance requirements by enforcing least privilege access and providing detailed audit logs.
- Accountability: With PIM, every action can be traced back to an individual, increasing accountability and making it easier to track changes and access patterns.
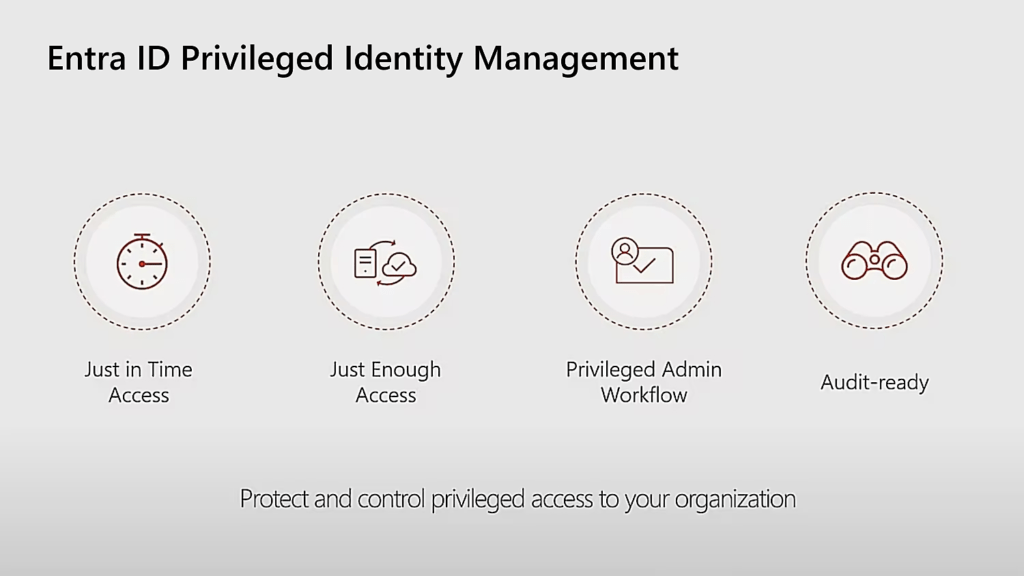
Key Features of Azure Entra ID PIM
- Just-in-Time Access: Users can request temporary access to perform tasks, which is automatically revoked after a set period.
- Approval Workflow: Access requests can be configured to require approval from designated reviewers.
- MFA Enforcement: Multi-Factor Authentication (MFA) can be required for activation of privileged roles.
- Access Reviews: Regular reviews of access permissions can be scheduled to ensure they are still needed.
- Audit and Alerts: Comprehensive logging and alerting on privileged activities provide visibility into what’s happening in your environment.
Use Case: Simplifying Access Management
Let’s consider an example to illustrate how PIM can be beneficial.
Scenario: Your company, Acme Corp, has a team of IT administrators who occasionally need access to manage the Azure infrastructure. However, continuous access poses a security risk.
Solution with PIM:
- Setup Roles: Define roles within PIM for the different types of administrative tasks (e.g., VM management, network configuration).
- Assign Roles: Assign these roles to the respective administrators but keep them in an inactive state.
- Just-in-Time Activation: When an admin needs to perform a task, they request access through PIM. The request can be set to require approval and enforce MFA.
- Monitor and Audit: Use PIM’s audit logs to track all privileged access and actions taken, ensuring compliance and accountability.
By using PIM, Acme Corp can ensure that administrators have the access they need only when necessary, significantly reducing security risks and helping maintain compliance.
Getting Started with PIM
To get started with Azure Entra ID PIM:
- Enable PIM: Navigate to Azure Entra ID in the Azure portal and enable PIM.
- Define Roles and Policies: Configure the roles and policies that suit your organisation’s needs.
- Assign Users: Assign users to roles with the appropriate activation requirements.
- Monitor and Review: Regularly monitor access and perform access reviews to ensure ongoing security and compliance.
Azure Entra ID Privileged Identity Management is an essential tool for any organisation looking to enhance its security posture by managing access to critical resources efficiently and effectively.
By adopting Azure Entra ID PIM, organisations can reduce the risks associated with permanent elevated access, ensure compliance, and maintain a higher level of security. It’s a proactive step towards a more secure and well-managed IT environment.
For more information, you can refer to Microsoft’s documentation on PIM and Azure Entra ID.