In the digital era, protecting data is not just a priority; it’s an imperative. Microsoft Azure, a leading cloud service provider, offers a suite of tools and features to ensure that your data is not only stored efficiently but also protected with the highest standards of security. This guide will delve into the data protection and security features available in Azure Storage, providing insights on how to secure your data against various threats.
Why Data Protection and Security are Crucial
Data breaches and cyber threats are on the rise, making data protection a critical concern for businesses. Advanced data protection and security in Azure Storage are essential for:
- Compliance: Meeting regulatory requirements such as GDPR, HIPAA, and CCPA.
- Trust: Build and maintain trust with customers by ensuring their data is safe.
- Business Continuity: Protecting against data loss and ensuring data availability.
Now, let’s explore the advanced features Azure provides to secure your data.
1. Encryption at Rest and in Transit
Azure ensures that your data is always encrypted, whether it is at rest or in transit.
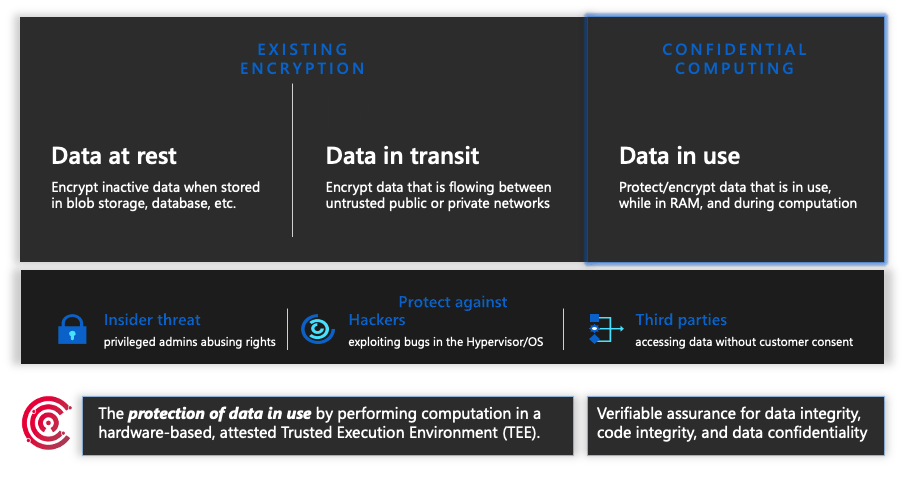
Encryption at Rest: Azure Storage automatically encrypts your data when it is written to the cloud. This is achieved using Storage Service Encryption (SSE) with Azure-managed keys. Alternatively, you can manage your own keys using Azure Key Vault. for example A financial institution handling sensitive customer data can use Azure Key Vault to manage encryption keys, ensuring that only authorised personnel have access to these keys and enhancing the security of encrypted data.
Encryption in Transit: Data moving between your application and Azure Storage is encrypted using HTTPS. Azure also supports client-side encryption, where data is encrypted before it is sent to Azure Storage.
2. Advanced Threat Protection
Azure provides advanced threat protection for your storage accounts, helping you detect and respond to potential threats in real-time.
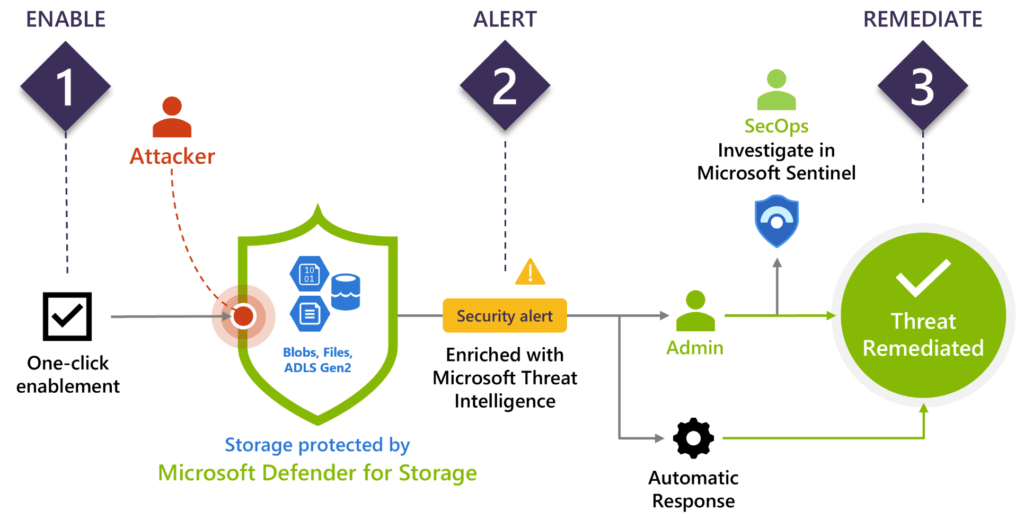
Microsoft Defender for Storage: Microsoft Defender for Storage monitors your data and provides alerts for suspicious activities, such as unusual access patterns or potential malware uploads. It integrates seamlessly with Azure Security Center, providing a unified view of security across your Azure environment. For example, an e-commerce platform can use Azure Defender to monitor for unusual activity, such as a sudden spike in read operations, which could indicate a data exfiltration attempt. Automated alerts enable quick response to mitigate potential threats.
3. Data Access Control
Controlling who has access to your data is crucial for security. Azure provides several mechanisms to ensure robust access control.
Role-Based Access Control (RBAC) : Azure RBAC allows you to assign specific permissions to users, groups, and applications. By following the principle of least privilege, you can ensure that users have only the access they need to perform their tasks. For instance, a healthcare organisation can implement RBAC to ensure that only authorised medical staff have access to patient records, while administrative personnel have access to non-sensitive data only.
Shared Access Signatures (SAS): SAS tokens provide limited access to your storage resources without exposing your account key. You can specify the permissions and the duration for which the access is granted. As an example a software development team can use SAS tokens to grant temporary access to external contractors, allowing them to upload code to a specific container without granting broader access to other resources.
4. Network Security
Securing the network path to your storage resources is another layer of defence.
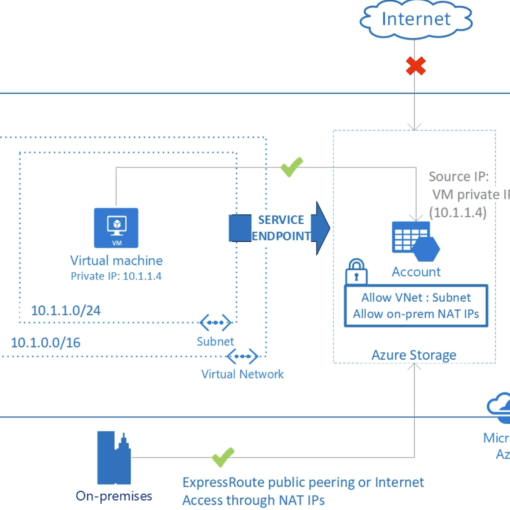
Virtual Network Service Endpoints: Service endpoints allow you to restrict access to your storage accounts from specific virtual networks. This ensures that your storage resources are not exposed to the public internet, reducing the risk of unauthorised access. As a case in point, A large corporation can use service endpoints to ensure that only virtual machines within its virtual network can access sensitive storage accounts, providing an additional layer of security.
Private Endpoints: Private endpoints allow you to connect to Azure Storage via a private IP address within your virtual network. This ensures that traffic between your virtual network and Azure Storage remains on the Microsoft backbone network, enhancing security and reducing exposure to the internet.
5. Data Backup and Recovery
Ensuring data availability and recoverability in case of accidental deletion or corruption is a critical aspect of data protection.
Azure Backup: Azure Backup provides simple and reliable backups for your data stored in Azure Storage. It supports automated backup schedules and retention policies, ensuring that your data is protected against accidental deletion and corruption.
Point-in-Time Restore: Point-in-Time Restore allows you to restore your Azure Blob Storage data to a previous state at a specific point in time. This feature is particularly useful for recovering from accidental data modifications or deletions.
Azure Storage offers a comprehensive suite of advanced data protection and security features designed to safeguard your data against threats and ensure compliance with regulatory requirements. By leveraging encryption, advanced threat protection, data access control, network security, and robust backup and recovery solutions, you can enhance the security of your data and maintain the trust of your customers.
Optimising these features is not a one-time task but an ongoing process. Regularly review and update your security configurations to adapt to evolving threats and ensure that your data remains secure.
Sources:
- Microsoft Azure Documentation: Azure Storage Security Guide
- Azure Security Center: Advanced Threat Protection for Azure Storage
- Azure Key Vault: Manage Your Own Encryption Keys
Feel free to reach out with any questions or additional topics you’d like to explore. Stay secure and happy data storing!