Updated – June 2024
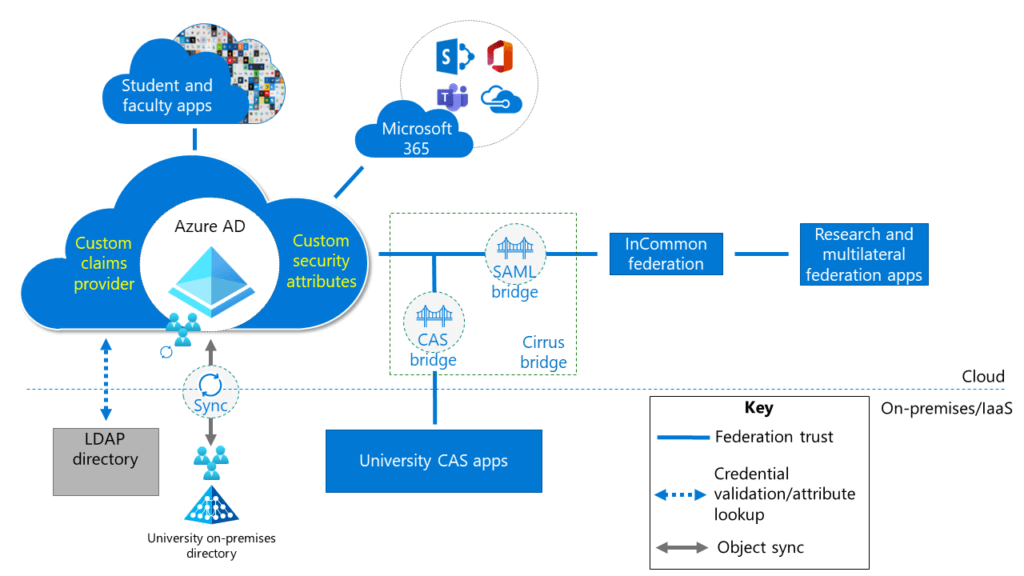
Azure Entra ID (formerly known as Azure Active Directory) is a cloud-based identity and access management service from Microsoft. It offers a wide range of features designed to help organisations manage identities, secure access, and ensure compliance. In this post, we’ll explore the core services and features of Azure Entra ID, including Privileged Identity Management (PIM), Access Reviews, Entitlement Management, Conditional Access, and more.
What is Azure Entra ID?
Azure Entra ID is a comprehensive identity management solution that provides single sign-on, multi-factor authentication, and conditional access to guard against cybersecurity threats. It helps organisations manage and secure identities for employees, partners, and customers, ensuring that only authorised users can access resources.
Some of the Core Services:
- Privileged Identity Management (PIM)
- Access Reviews
- Entitlement Management
- Conditional Access
- Identity Protection
- Self-Service Password Reset (SSPR)
- Azure AD B2B (Business to Business)
- Azure AD B2C (Business to Consumer)
1. Privileged Identity Management (PIM)
Privileged Identity Management (PIM) is a service that helps organisations manage, control, and monitor access to important resources within Azure Entra ID, Azure, and other Microsoft Online Services.
Key Features:
- Just-in-Time Access: Users can request temporary privileged access when needed, reducing the risk of long-term exposure.
- Approval Workflow: Access requests can go through an approval process to ensure that only authorised users gain access.
- Time-bound Access: Privileged access is granted for a limited duration, further reducing risk.
- Access Reviews: Regularly review access permissions to ensure they are still necessary.
- Audit History: Keep track of all privileged access activities for auditing and compliance purposes.
2. Access Reviews
Access Reviews in Azure Entra ID help organisations ensure that only the right users have access to resources. Regularly reviewing access permissions helps maintain security and compliance.
Key Features:
- Scheduled Reviews: Set up periodic access reviews to ensure ongoing compliance.
- Automated Reviews: Automatically initiate reviews based on certain criteria, such as user inactivity.
- Review Delegation: Delegate review responsibilities to managers or resource owners.
- Insights and Reporting: Get detailed insights and reports on access review outcomes.
3. Entitlement Management
Entitlement Management helps streamline the process of managing access to groups, applications, and resources by providing a way to manage access lifecycle policies.
Key Features:
- Access Packages: Create packages that bundle resources and permissions, making it easy to assign access based on roles or projects.
- Lifecycle Management: Automate the process of granting, reviewing, and revoking access.
- Access Requests: Allow users to request access to resources, with approval workflows to manage these requests.
- External User Collaboration: Simplify access for external partners and collaborators.
4. Conditional Access
Conditional Access policies provide a way to control access to resources based on specific conditions, enhancing security by enforcing different controls based on user context.
Key Features:
- Risk-Based Access: Evaluate user risk levels and enforce different access controls based on risk.
- Device Compliance: Ensure that only compliant devices can access resources.
- Location-Based Access: Restrict access based on user location, such as blocking access from high-risk locations.
- Session Controls: Control what users can do during a session, such as limiting access to sensitive data.
5. Identity Protection
Identity Protection uses machine learning and heuristics to detect suspicious actions related to user identities and take automated actions to mitigate risks.
Key Features:
- Risk Detection: Identify risky sign-ins and user activity.
- Automated Responses: Take automated actions such as requiring password changes or enforcing multi-factor authentication.
- User Risk Policies: Define policies to respond to detected risks.
6. Self-Service Password Reset (SSPR)
Self-Service Password Reset (SSPR) enables users to reset their passwords on their own, reducing helpdesk calls and improving user productivity.
Key Features:
- User Verification: Users must verify their identity using alternate contact methods before resetting their password.
- Multi-Factor Authentication: Integrate SSPR with multi-factor authentication for added security.
- Customisation: Customise the password reset experience to align with organisational policies.
7. Azure AD B2B (Business to Business)
Azure AD B2B allows organisations to securely share applications and services with guest users from any other organisation while maintaining control over their own corporate data.
Key Features:
- Guest Access: Invite external users to collaborate on internal resources.
- Customisable Access: Define access permissions for guest users based on their role or relationship.
- Secure Collaboration: Ensure that guest access adheres to your organisation’s security policies.
8. Azure AD B2C (Business to Consumer)
Azure AD B2C provides identity and access management solutions for consumer-facing applications, allowing you to authenticate and manage users from various identity providers.
Key Features:
- Customisable User Journeys: Create tailored sign-up and sign-in experiences for consumers.
- Multi-Provider Support: Authenticate users with various identity providers like Google, Facebook, or Microsoft accounts.
- Scalability: Handle millions of consumer identities with robust security and performance.
Azure Entra ID provides a comprehensive set of identity management features and core services designed to enhance security, ensure compliance, and improve operational efficiency. By leveraging services like PIM, Access Reviews, Entitlement Management, Conditional Access, and others, organisations can effectively manage and secure their identities and access to resources.
Sources: